How to Exploit Code Injection Vulnerabilities in Serverless Goat
Cloud-Native and Serverless applications are trending models for developing cloud applications as they provide …

More and more organizations rely on cloud services or even start fully shifting to cloud-native. Thus, so-called Cloud Security Posture Management (CSPM) tools and technologies have become popular since they aim to reduce and manage security risks in the cloud.
Companies are shifting their workloads to the cloud - for a good reason - it reduces the cost and time-to-market, while increasing development speed. However, the shift to the cloud does not come for free. Many companies are struggling to monitor and check the secure configuration of their cloud environments due to the fast pace at which cloud infrastructures change. Surely, the use of multiple cloud providers and the combination of private and public clouds does not make tracking down misconfigurations an easy task. In fact, a leading cause of data breaches are cloud (security) misconfigurations, enabling data breaches like the Advantage Capital Funding and Argus Capital Funding breach in 2020, and can go as far as corrupting the company network, as described in our article Five Common Cloud Security Threats.
CSPM tools aim to detect such misconfigurations, warn the security team, and help fix and patch issues before attackers can exploit them.
Cloud misconfigurations can happen easily, a developer or DevOps engineer may unknowingly miss to set a particular option or unintentionally misconfigure it, e.g., not set up a multi-factor authentification or miss encrypted S3 buckets. A CSPM tool checks cloud users and cloud resources for such misconfigurations. Typical misconfigurations are, for instance, unencrypted data storages, open databases, accounts with high permissions, or deactivated security controls.
A manual approach for checking an account for misconfigurations cannot keep up with the rapid changes in today’s cloud environments which Infrastructure-as-Code technologies make possible. Such an approach becomes even more infeasible when trying to secure multiple accounts or even multiple cloud providers. To manage cloud resources and issues effectively and to stay on top of new assets added to your cloud environment, it is inevitable to use automated CSPM tools that continuously monitor your cloud.
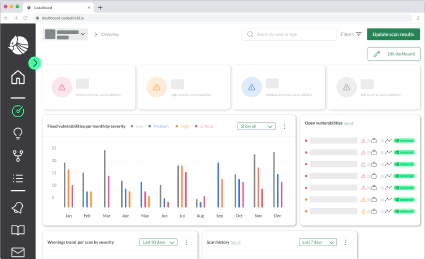
A single AWS account comprises dozens of different accounts, dozens of regions, and hundreds or thousands of different cloud resources, e.g., networks, databases, S3 buckets, users, making it difficult to keep track of all the used resources or which user has access to each resource. In addition, the large amount of resources makes it difficult to identify unused resources that are still active and running, but unused, thusly costing money. To cope with that issue, a CSPM tool must provide a comprehensive overview of all resources in the cloud for the security team.
A problem that comes up with many CSPM tools is their lack of context. A CSPM tool checking for misconfigurations or - in the best case displaying also CVEs - produces a sheer amount of noise, leaving the tasks to triage thousands of warnings to the security team. However, merely raising a warning for a potential security issue is not enough. The key question is “Is my cloud exploitable given the way the cloud resource is affected by the warning?” or - simply put - Is the security issue actually exploitable in my cloud environment?". To answer this question, next-generation CSPM tools must analyze and respect the context of a security issue by taking into account which resources are also impacted if the issue is exploited.
There are a lot of things a cloud security team can do to improve security - however, the tough part is to choose what to do. To ease the decision which issues must be addressed immediately, the raised warnings must be prioritized with respect to their context, business impact, and exposure of the affected resource.
A simple CSPM has become a must-have to manage and secure the cloud environment. To scale with today’s multi-account environments and to reduce noise, CSPM tools have to contextualize and prioritize security warnings to guide and support security teams efficiently.

Cloud-Native and Serverless applications are trending models for developing cloud applications as they provide …

One of the more infamous examples of the impact of vulnerable software components is the data breach of the …

More and more companies are moving their workloads to the cloud - and for a good reason: it reduces the cost …