Cloud-Developers worldwide trust CodeShield
What People Say
Testimonials
1-Click Graph View
Discover Critical Privilege Escalations
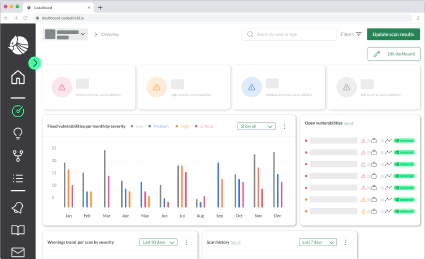
CodeShield identifies IAM privilege escalation vulnerabilities and attack paths, that attackers can use to exploit your cloud, and classifies them according to the MITRE ATT&CK. While misconfigurations, vulnerabilities, or over-permissioned IAM policies can be dangerous on their own, successful attacks are built on combinations of multiple weaknesses. CodeShield reveals hidden connections, and checks if there are dangerous IAM policies that allow an attacker to further move or pivot inside your cloud.
Speed up Cloud Development
Detect Breaking Changes Pre-Deployment
See what’s breaking before deploying infrastructure-as-code changes to your cloud.
- Determine the concrete impact of code changes to cloud resources
- Understand effective IAM permissions in code and cloud
- Increase security and prevent IAM privilege escalations even pre-deployment
Easy Risk Assessment
Cloud Impact Assessment
For every privilege escalation and attack scenario, CodeShield showcases which concrete cloud resources are at risk, this allows one to quickly identify which escalation to prioritize.
So you can quickly assess the impact of any finding and get an overview what resources an attack may compromise.
Our supporters
See how attackers see your cloud,
and learn how to stop them
Uncover attack paths and IAM policies allowing for privilege escalation.
Try now